AWS PrivateLink for DynamoDB
With AWS PrivateLink for DynamoDB, you can provision interface Amazon VPC endpoints (interface endpoints) in your virtual private cloud (Amazon VPC). These endpoints are directly accessible from applications that are on premises over VPN and AWS Direct Connect, or in a different AWS Region over Amazon VPC peering. Using AWS PrivateLink and interface endpoints, you can simplify private network connectivity from your applications to DynamoDB.
Applications in your VPC do not need public IP addresses to communicate with DynamoDB interface VPC endpoints for DynamoDB operations. Interface endpoints are represented by one or more elastic network interfaces (ENIs) that are assigned private IP addresses from subnets in your Amazon VPC. Requests to DynamoDB over interface endpoints stay on the Amazon network. You can also access interface endpoints in your Amazon VPC from on-premises applications through AWS Direct Connect or AWS Virtual Private Network (AWS VPN). For more information about how to connect your Amazon VPC with your on-premises network, see the AWS Direct Connect User Guide and the AWS Site-to-Site VPN User Guide.
For general information about interface endpoints, see Interface Amazon VPC endpoints (AWS PrivateLink) in the AWS PrivateLink Guide.
Topics
- Types of Amazon VPC endpoints for Amazon DynamoDB
- Considerations when using AWS PrivateLink for Amazon DynamoDB
- Creating an Amazon VPC endpoint
- Accessing Amazon DynamoDB interface endpoints
- Accessing DynamoDB tables and control API operations from DynamoDB interface endpoints
- Updating an on-premises DNS configuration
- Creating an Amazon VPC endpoint policy for DynamoDB
Types of Amazon VPC endpoints for Amazon DynamoDB
You can use two types of Amazon VPC endpoints to access Amazon DynamoDB: gateway endpoints and interface endpoints (by using AWS PrivateLink). A gateway endpoint is a gateway that you specify in your route table to access DynamoDB from your Amazon VPC over the AWS network. Interface endpoints extend the functionality of gateway endpoints by using private IP addresses to route requests to DynamoDB from within your Amazon VPC, on premises, or from an Amazon VPC in another AWS Region by using Amazon VPC peering or AWS Transit Gateway. For more information, see What is Amazon VPC peering? and Transit Gateway vs Amazon VPC peering.
Interface endpoints are compatible with gateway endpoints. If you have an existing gateway endpoint in the Amazon VPC, you can use both types of endpoints in the same Amazon VPC.
|
Gateway endpoints for DynamoDB |
Interface endpoints for DynamoDB |
|---|---|
|
In both cases, your network traffic remains on the AWS network. |
|
|
Use Amazon DynamoDB public IP addresses |
Use private IP addresses from your Amazon VPC to access Amazon DynamoDB |
|
Do not allow access from on premises |
Allow access from on premises |
|
Do not allow access from another AWS Region |
Allow access from an Amazon VPC endpoint in another AWS Region by using Amazon VPC peering or AWS Transit Gateway |
|
Not billed |
Billed |
For more information about gateway endpoints, see Gateway Amazon VPC endpoints in the AWS PrivateLink Guide.
Considerations when using AWS PrivateLink for Amazon DynamoDB
Amazon VPC considerations apply to AWS PrivateLink for Amazon DynamoDB. For more information, see Interface endpoint considerations and AWS PrivateLink quotas in the AWS PrivateLink Guide. In addition, the following restrictions apply.
AWS PrivateLink for Amazon DynamoDB does not support the following:
-
Transport Layer Security (TLS) 1.1
-
Private and Hybrid Domain Name System (DNS) services
AWS PrivateLink is currently not supported for Amazon DynamoDB Streams endpoints.
You can submit up to 50,000 requests per second for each AWS PrivateLink endpoint that you enable.
Note
Network connectivity timeouts to AWS PrivateLink endpoints are not within the scope of DynamoDB error responses and need to be appropriately handled by your applications connecting to the PrivateLink endpoints.
Creating an Amazon VPC endpoint
To create an Amazon VPC interface endpoint, see Create an Amazon VPC endpoint in the AWS PrivateLink Guide.
Accessing Amazon DynamoDB interface endpoints
When you create an interface endpoint, DynamoDB generates two types of endpoint-specific, DynamoDB DNS names: Regional and zonal.
-
A Regional DNS name includes a unique Amazon VPC endpoint ID, a service identifier, the AWS Region, and
vpce.amazonaws.comin its name. For example, for Amazon VPC endpoint IDvpce-1a2b3c4dvpce-1a2b3c4d-5e6f.dynamodb.us-east-1.vpce.amazonaws.com -
A Zonal DNS name includes the Availability Zone—for example,
vpce-1a2b3c4d-5e6f-us-east-1a.dynamodb.us-east-1.vpce.amazonaws.com
Endpoint-specific DynamoDB DNS names can be resolved from the DynamoDB public DNS domain.
Accessing DynamoDB tables and control API operations from DynamoDB interface endpoints
You can use the AWS CLI or AWS SDKs to access DynamoDB tables and control API operations through DynamoDB interface endpoints.
AWS CLI examples
To access DynamoDB tables or DynamoDB control API operations through DynamoDB interface endpoints
in AWS CLI commands, use the --region and --endpoint-url
parameters.
Example: Create a VPC endpoint
aws ec2 create-vpc-endpoint \ --region us-east-1 \ --service-name dynamodb-service-name \ --vpc-id client-vpc-id \ --subnet-ids client-subnet-id \ --vpc-endpoint-type Interface \ --security-group-ids client-sg-id
Example: Modify a VPC endpoint
aws ec2 modify-vpc-endpoint \ --region us-east-1 \ --vpc-endpoint-id client-vpc-endpoint-id \ --policy-document policy-document \ #example optional parameter --add-security-group-ids security-group-ids \ #example optional parameter # any additional parameters needed, see Privatelink documentation for more details
Example: List tables using an endpoint URL
In the following example, replace the Region us-east-1 and the DNS name of
the VPC endpoint ID vpce-1a2b3c4d-5e6f.dynamodb.us-east-1.vpce.amazonaws.com
with your own information.
aws dynamodb --region us-east-1 —endpoint https://vpce-1a2b3c4d-5e6f.dynamodb.us-east-1.vpce.amazonaws.com list-tables
AWS SDK examples
To access DynamoDB tables or DynamoDB control API operations through DynamoDB interface endpoints when using the AWS SDKs, update your SDKs to the latest version. Then, configure your clients to use an endpoint URL for accessing a table or DynamoDB control API operation through DynamoDB interface endpoints.
Updating an on-premises DNS configuration
When using endpoint-specific DNS names to access the interface endpoints for DynamoDB, you don’t have to update your on-premises DNS resolver. You can resolve the endpoint-specific DNS name with the private IP address of the interface endpoint from the public DynamoDB DNS domain.
Using interface endpoints to access DynamoDB without a gateway endpoint or an internet gateway in the Amazon VPC
Interface endpoints in your Amazon VPC can route both in-Amazon VPC applications and on-premises applications to DynamoDB over the Amazon network, as illustrated in the following diagram.
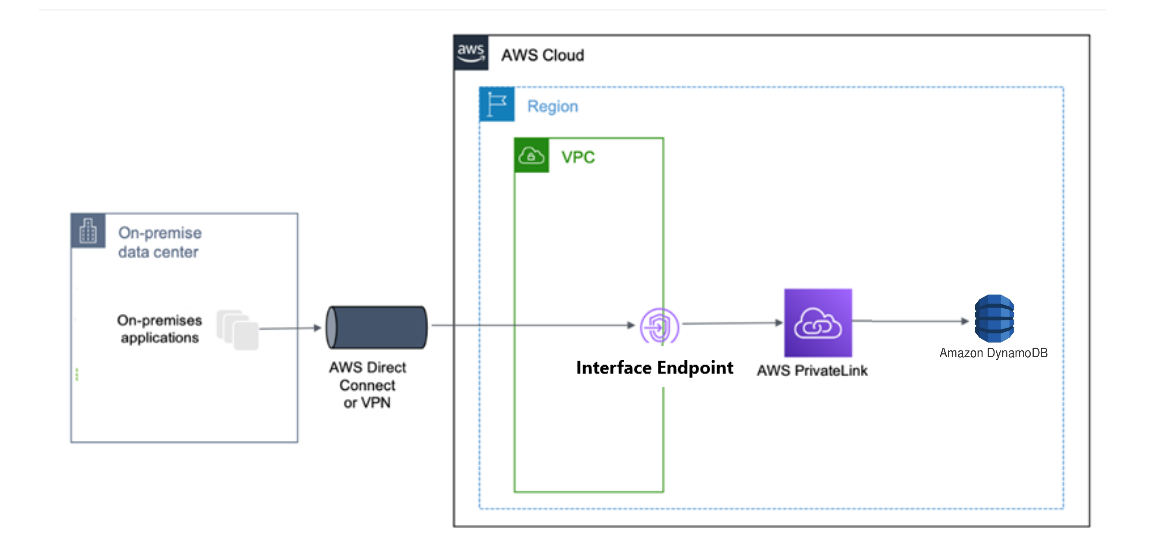
The diagram illustrates the following:
-
Your on-premises network uses AWS Direct Connect or AWS VPN to connect to Amazon VPC A.
-
Your applications on-premises and in Amazon VPC A use endpoint-specific DNS names to access DynamoDB through the DynamoDB interface endpoint.
-
On-premises applications send data to the interface endpoint in the Amazon VPC through AWS Direct Connect (or AWS VPN). AWS PrivateLink moves the data from the interface endpoint to DynamoDB over the AWS network.
-
In-Amazon VPC applications also send traffic to the interface endpoint. AWS PrivateLink moves the data from the interface endpoint to DynamoDB over the AWS network.
Using gateway endpoints and interface endpoints together in the same Amazon VPC to access DynamoDB
You can create interface endpoints and retain the existing gateway endpoint in the same Amazon VPC, as the following diagram shows. By taking this approach, you allow in-Amazon VPC applications to continue accessing DynamoDB through the gateway endpoint, which is not billed. Then, only your on-premises applications would use interface endpoints to access DynamoDB. To access DynamoDB this way, you must update your on-premises applications to use endpoint-specific DNS names for DynamoDB.
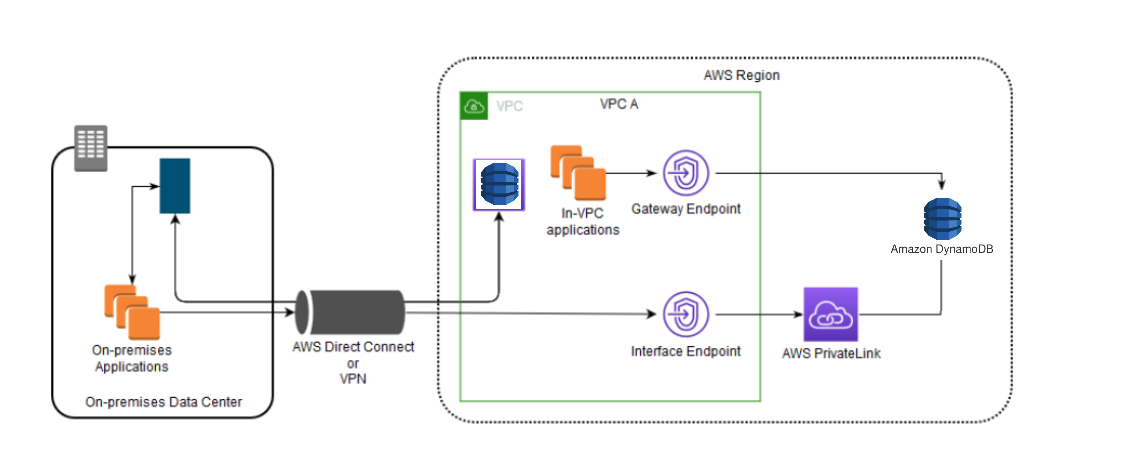
The diagram illustrates the following:
-
On-premises applications use endpoint-specific DNS names to send data to the interface endpoint within the Amazon VPC through AWS Direct Connect (or AWS VPN). AWS PrivateLink moves the data from the interface endpoint to DynamoDB over the AWS network.
-
Using default Regional DynamoDB names, in-Amazon VPC applications send data to the gateway endpoint that connects to DynamoDB over the AWS network.
For more information about gateway endpoints, see Gateway Amazon VPC endpoints in the Amazon VPC User Guide.
Creating an Amazon VPC endpoint policy for DynamoDB
You can attach an endpoint policy to your Amazon VPC endpoint that controls access to DynamoDB. The policy specifies the following information:
-
The AWS Identity and Access Management (IAM) principal that can perform actions
-
The actions that can be performed
-
The resources on which actions can be performed
Example: Restricting access to a specific table from an Amazon VPC endpoint
You can create an endpoint policy that restricts access to only specific DynamoDB tables.
This type of policy is useful if you have other AWS services in your Amazon VPC that use
tables. The following table policy restricts access to only the
DOC-EXAMPLE-TABLEDOC-EXAMPLE-TABLE
{ "Version": "2012-10-17", "Id": "Policy1216114807515", "Statement": [ { "Sid": "Access-to-specific-table-only", "Principal": "*", "Action": [ "dynamodb:GetItem", "dynamodb:PutItem" ], "Effect": "Allow", "Resource": ["arn:aws:dynamodb:::DOC-EXAMPLE-TABLE", "arn:aws:dynamodb:::DOC-EXAMPLE-TABLE/*"] } ] }